One of my biggest pet peeves is the return of the popup subscription box. Unlike the old popup/pop-under style Javascript boxes, you cannot easily prevent these from showing up. Usually, they are the incarnation of some desperate content site who will sell your email address to a hundred other soulless spam bots to keep their pathetic sites running. Worse yet, beyond these terrible annoyances that are flooding the web of click bait sites, you often times have numerous trackers, intrusive ads and hidden content that loads without your knowing nor permission. Many Ad Blockers these days just prevent the most dubious sites from phishing you or installing worms into your system. However, their subscription list often times are bought and paid for by the aforementioned groups, so there’s really little protection you can easily get without customizing your blocker. For those of you who actually care about not being tracked and having a cleaner web experience, this article is for you.
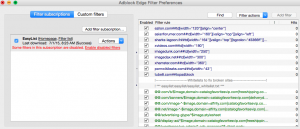
The big Ad Blockers basically are some form of html cleanser that removes pieces from a page or censors URLs based on some rules you use. If you ever open up your preferences, you’ll see a really crappy UI that looks like this:
If you notice the right side, you’ll see a huge list of green items. Those items are whitelisted sites and other expressions that typically come from the subscription you get on the left side of the interface. Unfortunately, from the UI there is no easy way to edit this list (and I’m certain they do this purposefully) outside of just individually unchecking each of those boxes.
The problem is that if you examine that list closely, you’ll notice some very shady sites, despite the fact that supposedly this thing ought to be blocking these sites. Yes, ad blockers with whitelisted sites containing stuff from porn sites for instance. So obviously, you cannot trust these lists right off the bat. It is up to you to modify them.
Although you can edit the file directly, most of the time it’s pretty clunky and not error proof without understanding the basic format. A slightly more tedious yet safe way I do things is through blocking items that I see on a site. The real problem is that even if you try to knock out all the whitelisted items, you can’t be 100% sure that what you’re blocking is legitimate or not. You might accidentally block a CDN that contains the CSS for a site and make the site unusable. So the task at hand does require an eye to attention.
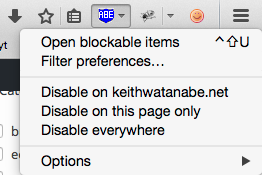
Usually, what I’ll do when blocking items is that I’ll go to a website and open up the blockable items. You can do this through clicking on the Ad Blocker icon, which should produce a submenu like this:
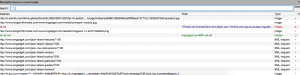
After that you can click on the “Open blockable items” line item and start to go to work. Doing that will produce a window at the bottom of the page and show you tons of URLs like this:
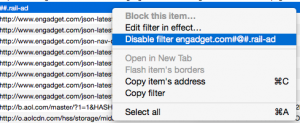
Notice the mixture of colored text. The most important things you should start scanning for are green items. These are whitelisted. If you start seeing odd ball ads floating around that dismay you, you need to disable the filter on them and then try to block them. Here’s an example:
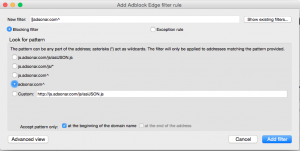
Now, comes the slightly more complex part. When you disable the filter, you can click the “Block this item” which will open up a new window like this:
So in this situation, I have several options listed by the radio items. Depending on the item, I might have to block a whole URL or block part of it. My rule of thumb is to block any URL that is not the same as the website you are visiting. Obviously, I don’t do this all the time. Sometimes, a website will use critical plugins like discus for comments. If I want to use those comments, I cannot block the external site. However, if you see words like “ads”, “omniture,” “pixel,” “tracking,” “beacon,” etc., then those are pretty much automatic red flags for stuff that either are whitelisted or stuff that haven’t been placed into the filter and you should probably block to avoid being tracked.
While that might take care of some of the basic external sites, you still might end up dealing with Javascript, popups and trackers that originate from the site in question. Most are loaded onto a CDN (content delivery network) which is used to make the page load faster. Now, this generally is a good thing but depending on how the site uses Javascript, you might have to block parts of the CDN too.
So this is where it gets really tricky. Generally, when I go to look at things I can filter, I filter my filters with the “js” search option. What that does is limits only the files and directories with the “js” letters to be found. Most Javascript files are named with the .js extension and stored under directories named with js, scripts or javascript. And the reason why I try to block these files is because these are the ones creating the annoying popups.
Here, basically, you want to try to write a rule that takes care of these files. Most of the time, the ad blocker rule will figure this out. However, because of these CDNs and the way companies might shrink files down with a special build process, blocking one directory might not be effective enough for your next visit. Sometimes you might get a file located on a CDN where one of the directories is named with a timestamp (which is essentially either a year-month-day-hour-minute-second naming convention or some other form to force your browser to refresh the cache with these files if they add new code to it). Also, the CDN might have different names too like a0.rackspace.com, s3.rackspace.com. Because these CDNs are built for redundancy (meaning if a bunch of servers go down they can fail safe mechanisms that will switch your location), you have to block a certain part of the CDN name.
So a complex rule might look like:
||rackspace.com/*/omniture/*
What this rule says is block anything beginning with the URL rackspace.com, be located in any directory matching up to the omniture keyword and block everything in that directory. In short, you would block the whole omniture directory on the CDN (where omniture is a tracking/analytics company).
But why block just the js files? Why not block more? The problem is that if you block too much, the site might become unusable. For instance, you might accidentally block .css or font files that make the site’s design workable. So you should never block those things, especially if they come from the site itself. The main thing is that you want to block the functionally annoying parts, which tend to originate from Javascript.
Now, I know people will say, “Doesn’t that hurt the website in question with regards to revenue that they might receive from ads?” Yes, which is why I will say that you should do this at your discretion. If you really want to support a site because they produce great content, block as little or as much as you want. Click on the ads on the site to demonstrate your support.
However, I will also say that websites should become more focused around user experience. Right now, the conflated tracking and 3rd party crap has bloated most websites to the point of becoming unusable. The constant popups, autoplaying/max volume videos, etc. are all horrible user experiences. Worse yet, many of these sites that claim to be content sites actually do not have great content to start. Instead, most of the worst sites are nothing but click bait sites which should be shoved back into the earth, their staff fired and sent to the sun as a science experiment for the betterment of mankind because these sites only pollute the internet with their garbage and stay afloat through nefarious means. If you hate ads and want to voice your opinion that reflect my own, don’t feel bad about helping to take these cancerous leech sites into the ground. There’s plenty of them and if one goes down, another five will spring up to replace it.